Happy Birthday, JiaTan and XZ: Why Your Software Supply Chain is Crazier Than You Think

It’s been one year since the discovery of the March 28th, 2024, XZ-utils breach and the attack that changed the open source ecosystem forever. Every day, developers around the world power a trillion-dollar global economy by contributing millions of pieces of open source code used by every organization to build and maintain their products. However, […]
How the Elf on the Shelf Messed Up My Software Supply Chain

With two young kids, the annual tradition of Elf on the Shelf is alive and well in my house. But, of course, the suspense and thrill of this beloved custom is taken to another level in the Smith household. It begins with the sudden appearance of a suspicious elf – usually the day after Thanksgiving […]
Where the Wild Things Are: A Complete Analysis of Jia Tan’s GitHub History and the XZ Utils Software Supply Chain Breach
Breaking down the recent XZ Utils security breach and how things came about.
Software Supply Chain Defense: Colorama, GitHub, and More
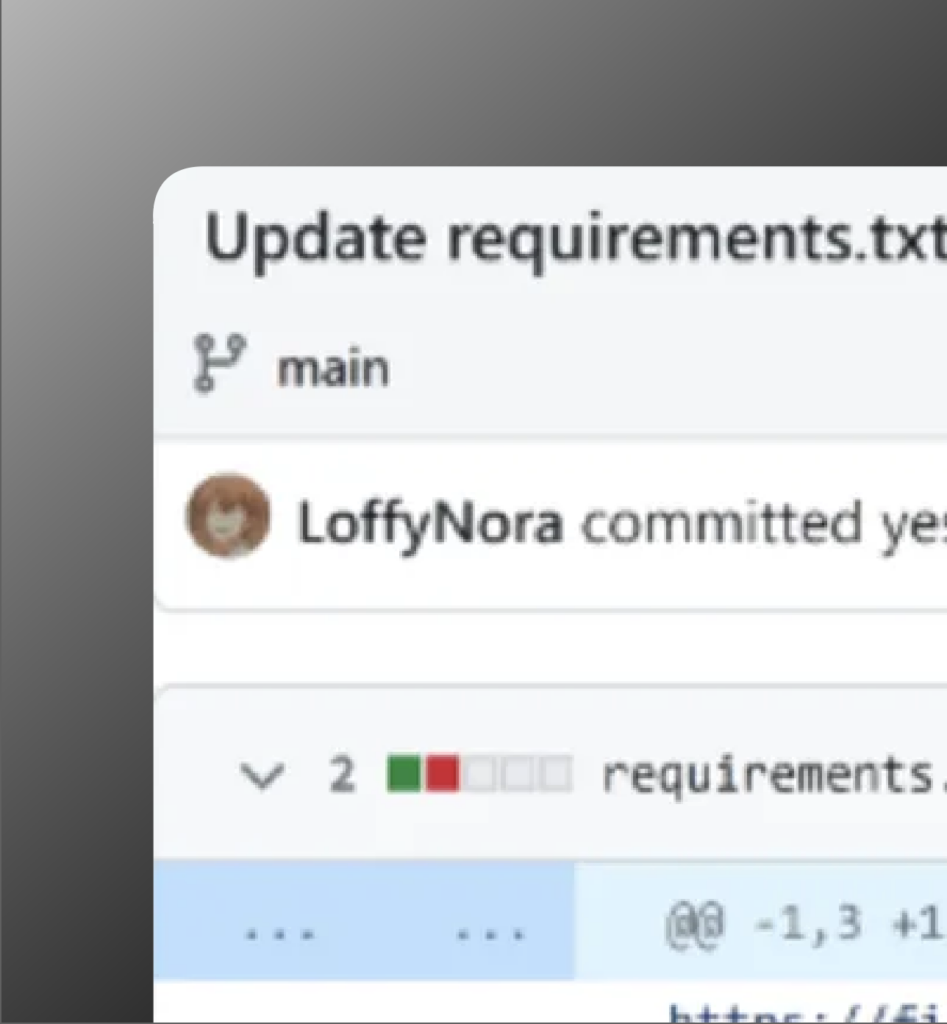
Lessons learned from the attack that targeted 170k+ GitHub users and some easy things your teams can do to protect their organization from the next one.
How SBOMs Help You Maneuver in the Cyber Kill Zone
The best open source tools centered around software bill of materials (SBOM) and software supply chain visibility to move your team out of the Cyber Kill Zone and into safety to prepare for the next threat.
CYBER KILL ZONE
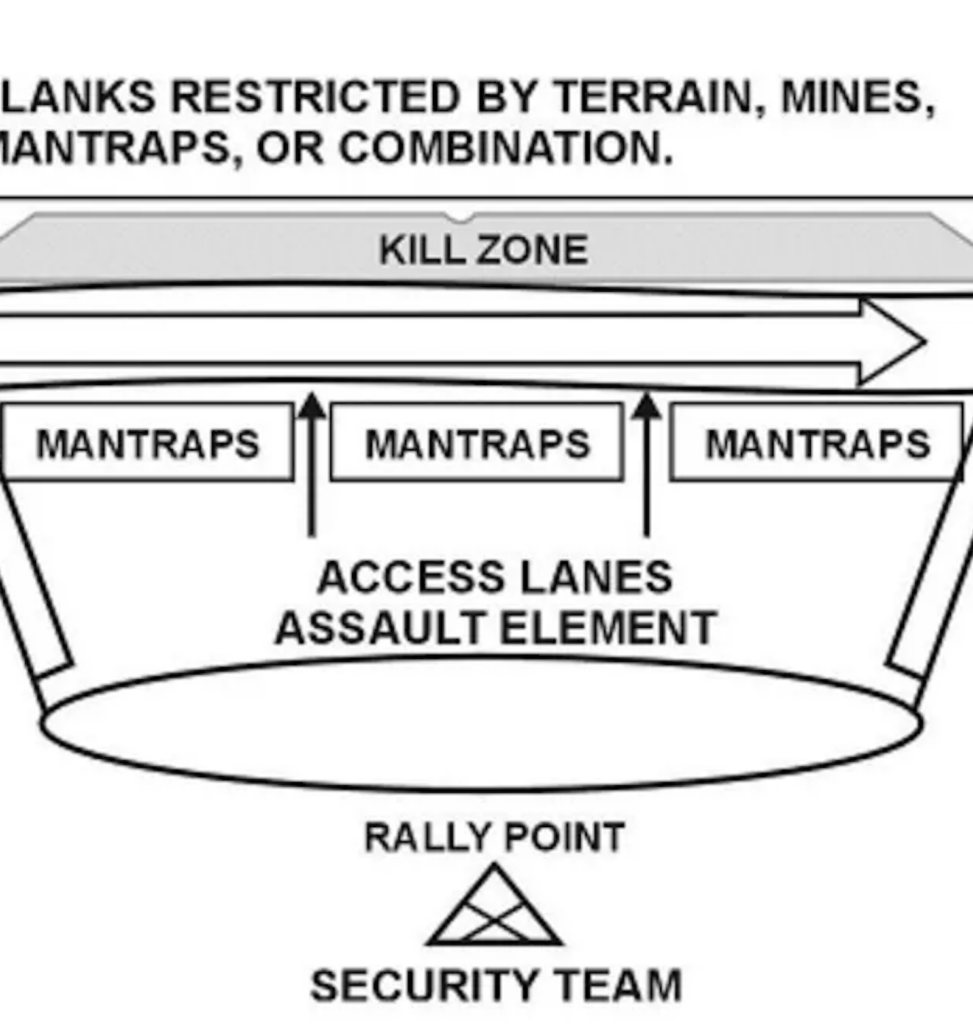
We quickly break down what a kill zone is historically, our definition of a Cyber Kill Zone at Hunted Labs, and the top five indicators your organization is sitting in a Cyber Kill Zone.

