DOMINATE SOFTWARE RISK
DOMINATE SOFTWARE RISK
DOMINATE SOFTWARE RISK
DOMINATE SOFTWARE RISK
WITH HUNTED LABS
The only AI-enabled platform designed to remove foreign influence in your software
DepsDiver
Reveal Dependency Risk in Seconds
Deep repository and dependency intelligence to help you identify the risks associated with external software packages with IDE extension available.
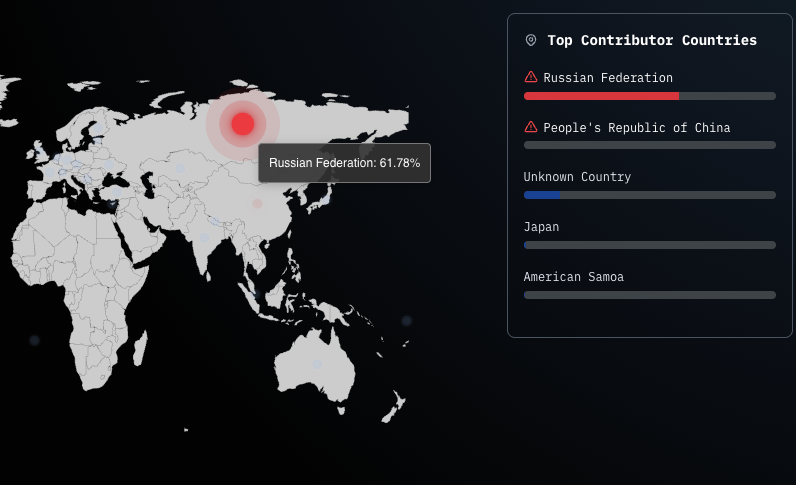
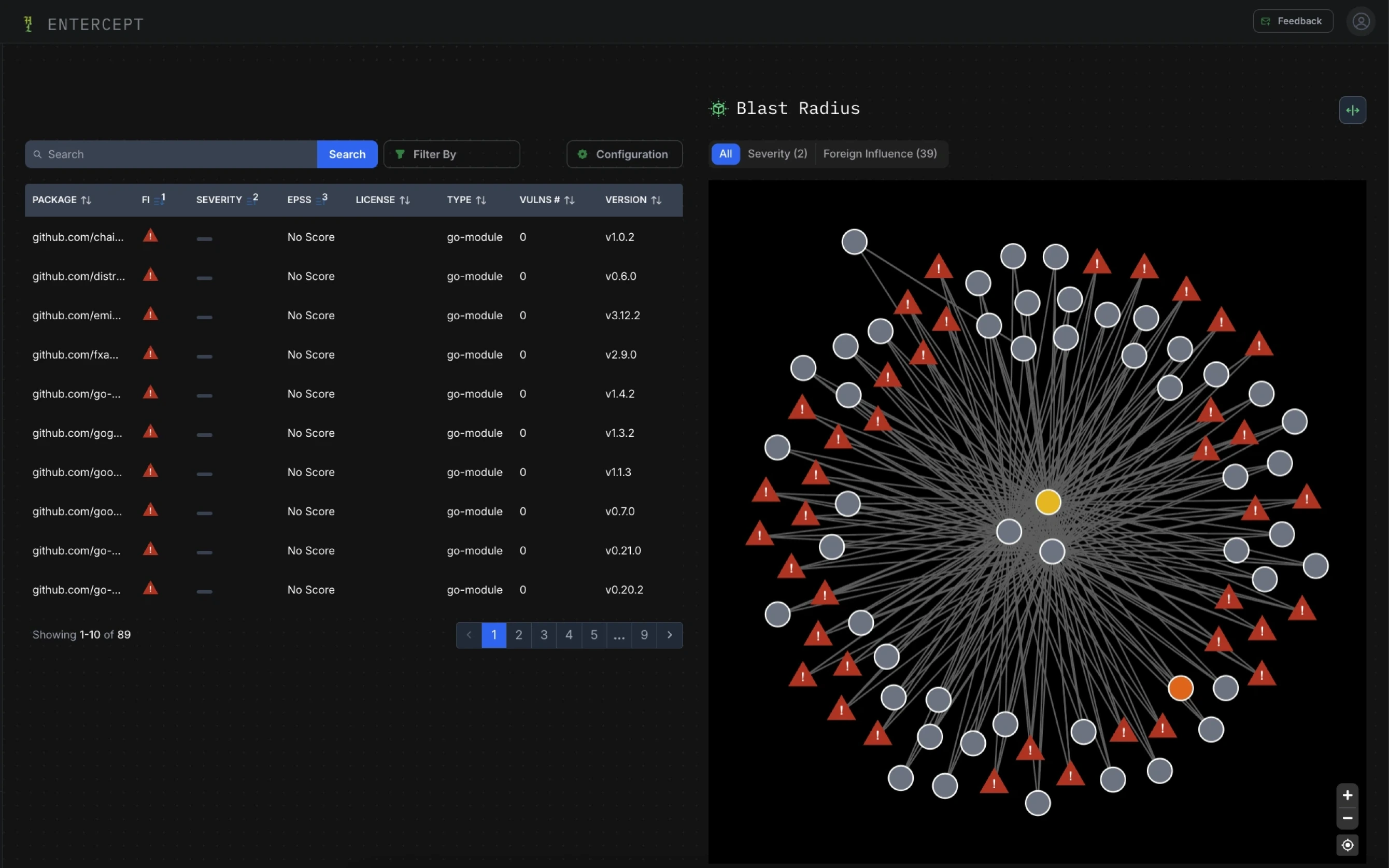
Entercept™
Secure What You Build, Continuously
Ongoing security monitoring and enforcement designed to prevent adversarial control across the software lifecycle.




















