Automated scanning at source and integrated into your CI/CD workflows
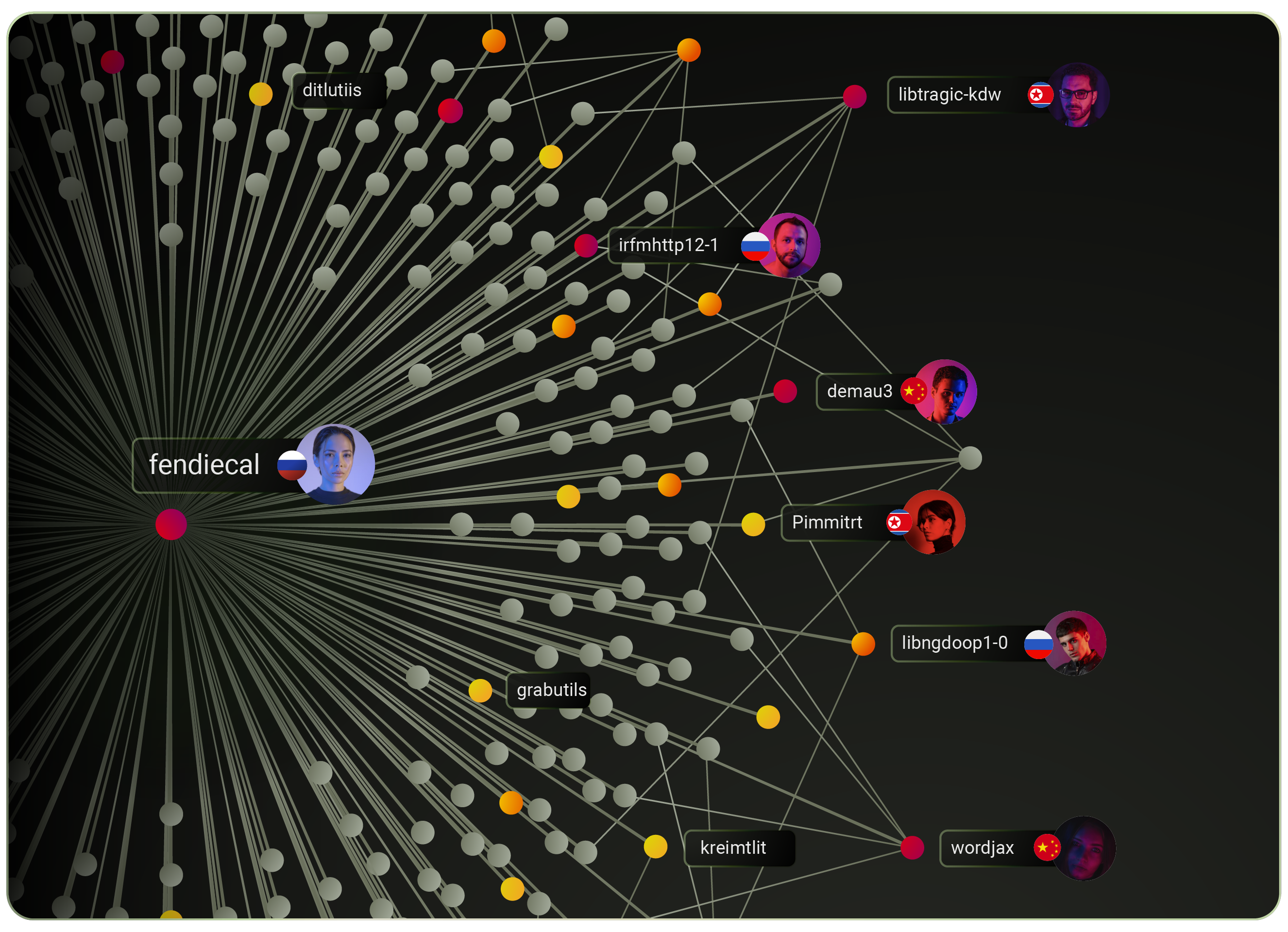
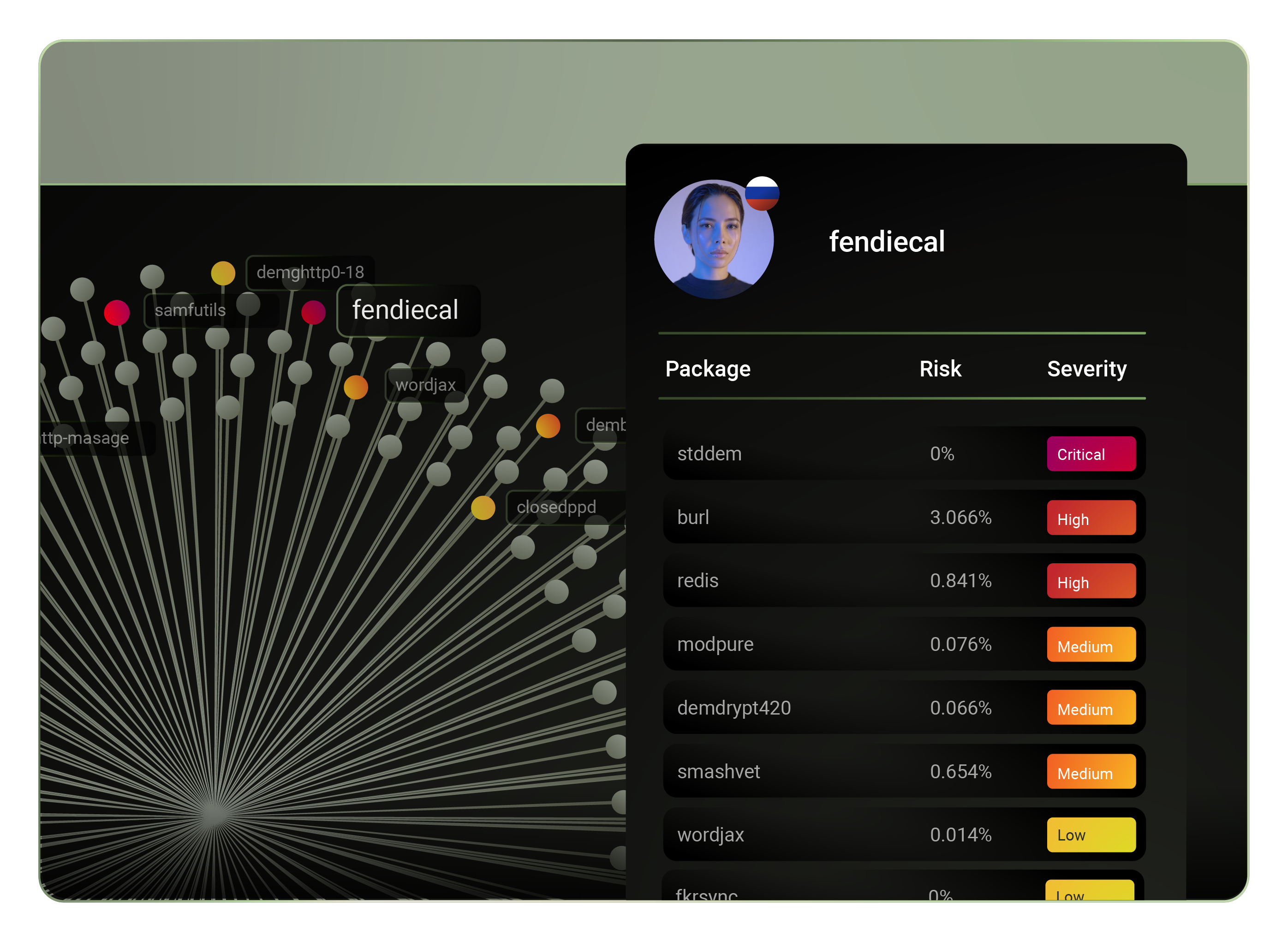

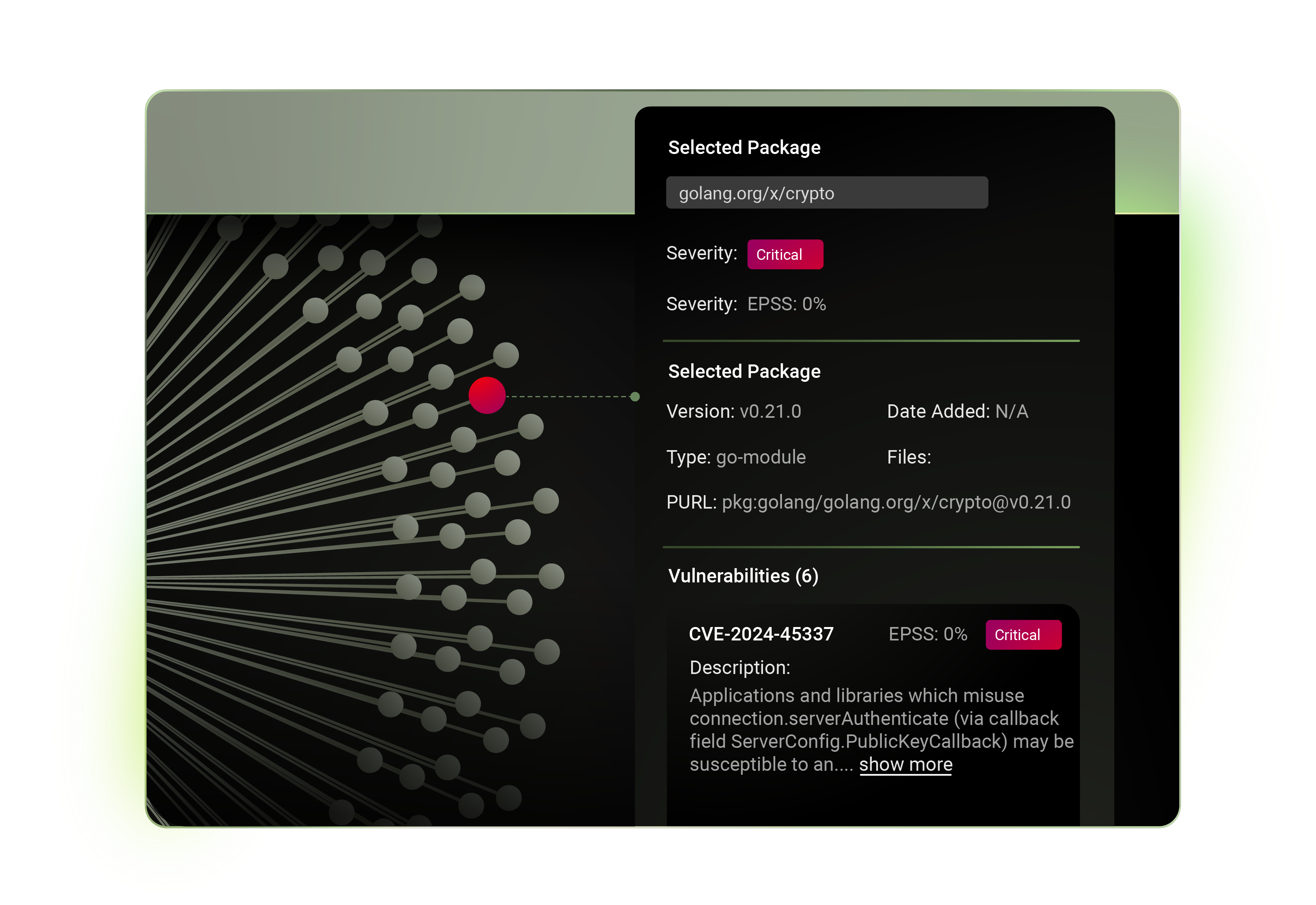
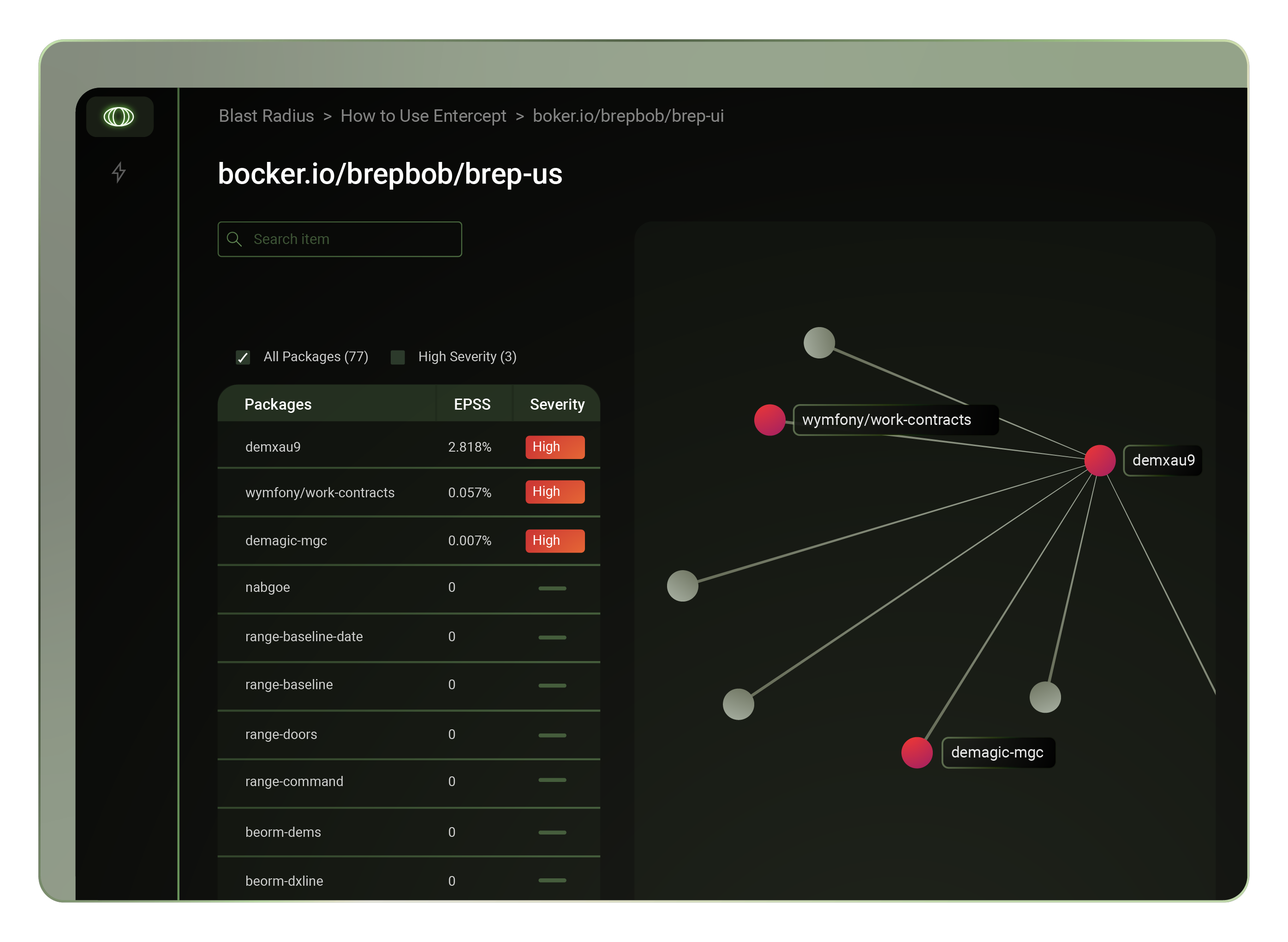
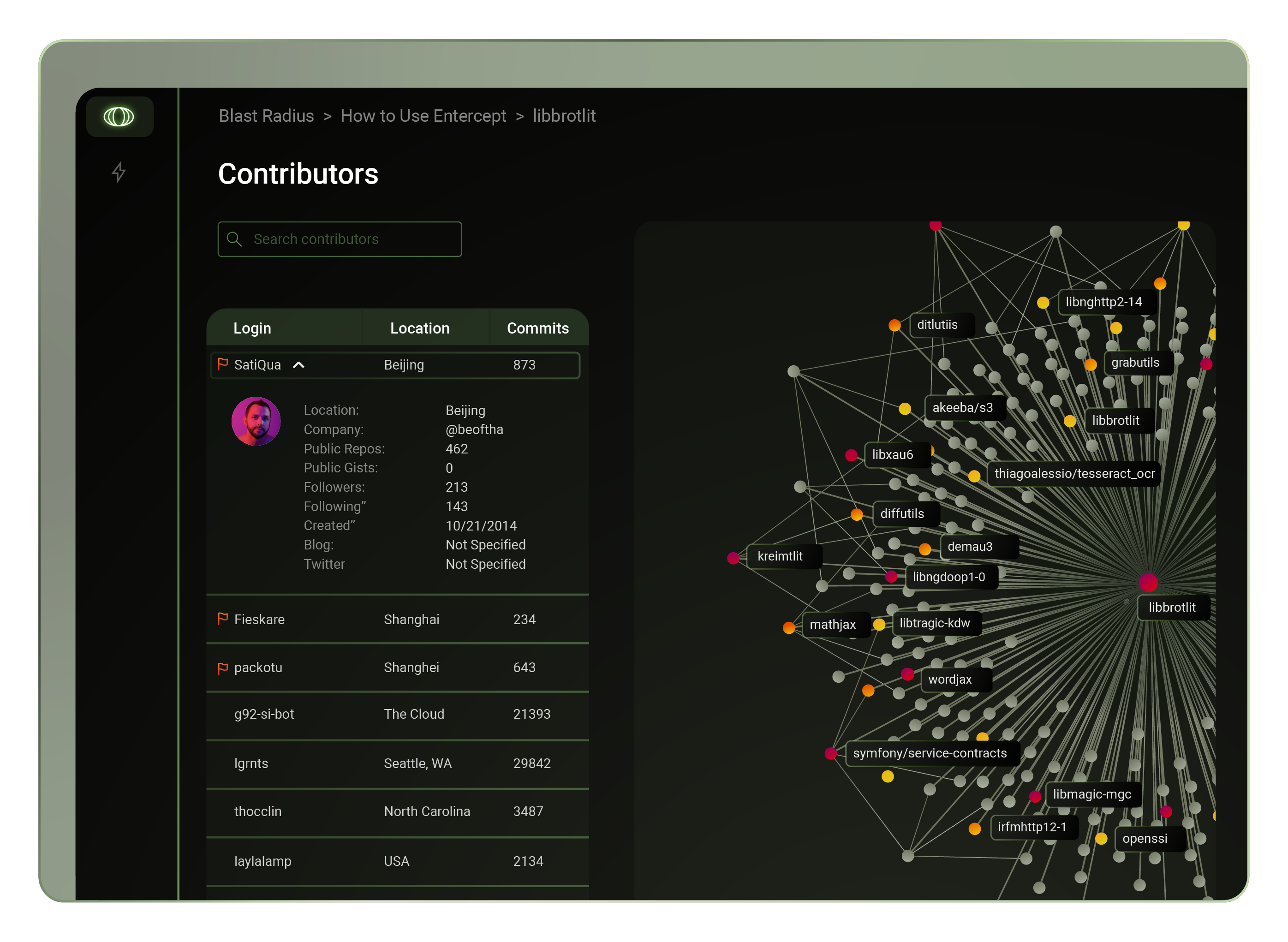
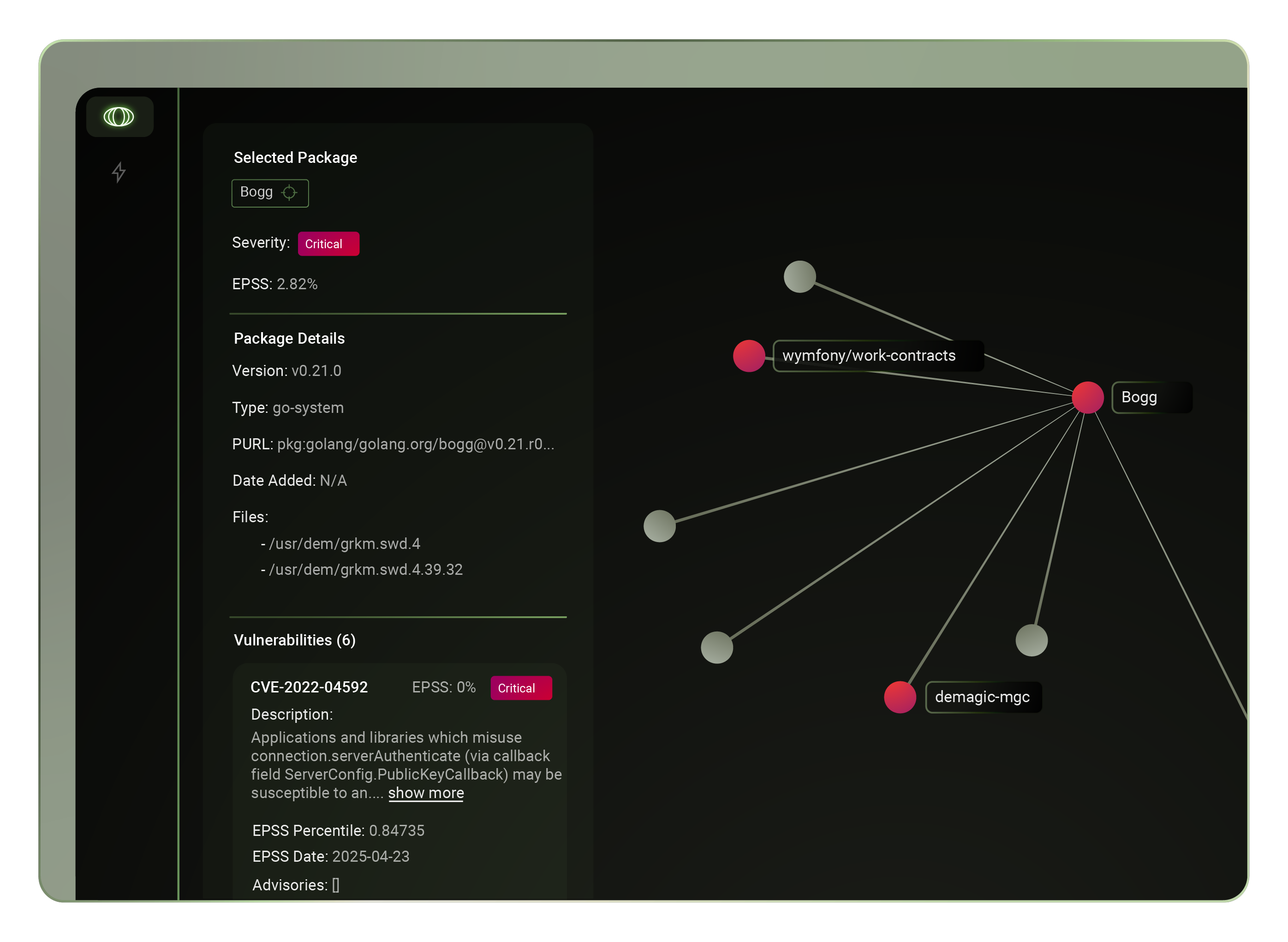
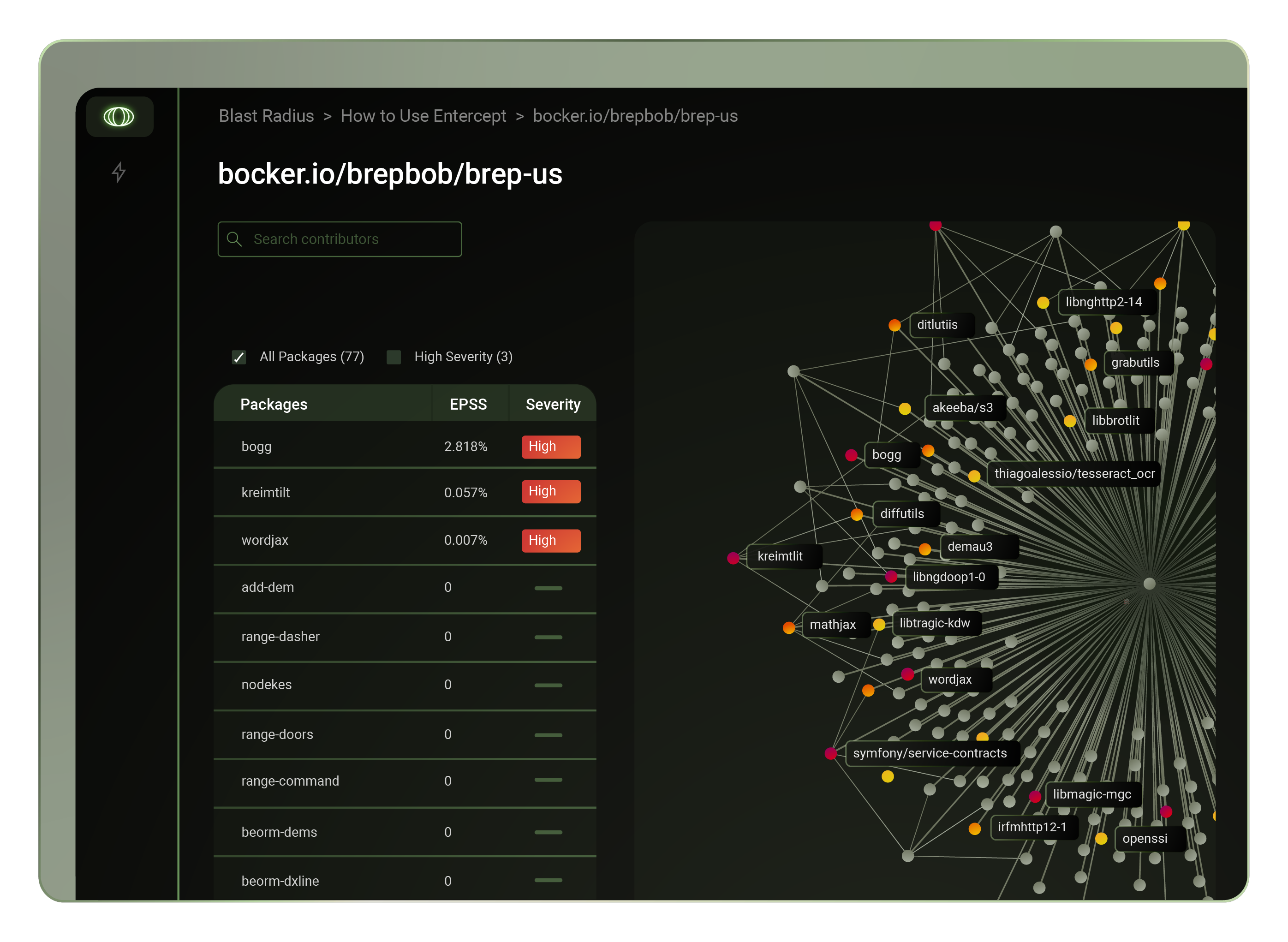
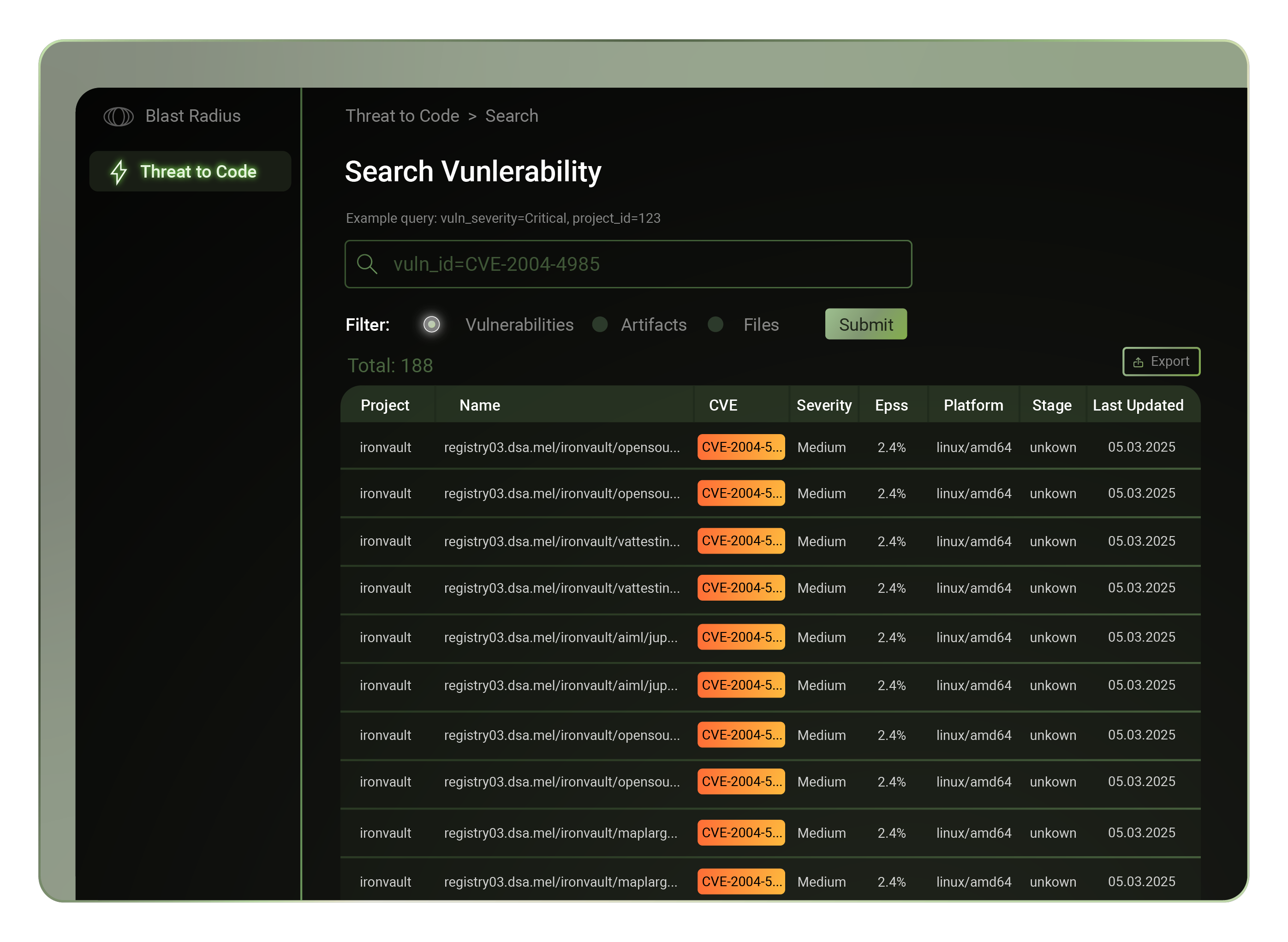

The following is a story about the recent XZ Utils security breach and how things came about. Formore context on the
Our Blog
Fill out the form below so we can arrange a product demo for you.
We have received your submission.