BATTLE TESTED. MISSION READY.
Understanding SBOMs and Your Software Attack Surface
Written by Tim Barone
Over the course of my career, I've seen a lot of cool technology, but I think most of us know in the cybersecurity community that the weakest link is typically the human. Many times that was in the form of performing security assessments and seeing how companies tracked inventory of components of their system or should I say failed to track. Back in the day, when it came to software, you were lucky to see an accurate list of software applications. Generally, it was listing out applications without understanding what they were actually composed of. I could also argue that most didn’t really know what software they had running in their environment(s).
Cut to today, as cyberattacks grow in sophistication and frequency, organizations must adopt robust strategies to mitigate risks effectively. Late last year, the Cybersecurity and Infrastructure Security Agency (CISA) released guidance on Software Bill of Materials (SBOM), offering a valuable framework to enhance cybersecurity practices. At Hunted Labs, we understand why SBOMs are important (it’s kinda our thing), and how organizations can leverage CISA's guidance to bolster their cybersecurity posture.
What is a Software Bill of Materials (SBOM)?
A Software Bill of Materials (SBOM) is a detailed inventory of software components used in a particular application or system. Similar to a traditional bill of materials in manufacturing, an SBOM provides a comprehensive list of all software elements, including open-source libraries, third-party components, and dependencies, along with their versions and sources. By providing visibility into the software supply chain, an SBOM helps organizations map their software attack surface, understand the composition of their software assets and assess each and every potential attack vector an attacker could leverage against them.
The Cyber Kill Zone emphasizes the importance of visualizing your software attack surface. This is the first step in understanding the threats present within your software, and more importantly, the relationships within all of the dependencies that helps you really start to understand the complexity of the blast radius with some of these software supply chain attacks that plague the headlines today. From our assessments and internal research, most organizations lack visibility into the components used in their applications, which can leave them vulnerable to various security threats, including supply chain attacks, software vulnerabilities, and license compliance issues. It’s important to note that failing to gain visibility into your software attack surface using SBOMs puts you on poor footing to establish an advantage over a software supply chain attack, which could actually start from an unintentional/unmalicious intention.
CISA's SBOM Guidance: Key Recommendations
In its SBOM guidance, CISA provides recommendations for organizations to create, maintain, and leverage SBOMs effectively. Some key recommendations include:
- Establish SBOM Requirements: Organizations should establish policies and procedures requiring the creation and maintenance of SBOMs for all software assets, including internally developed software and third-party applications.
- Automate SBOM Generation: Leveraging automated tools and processes for SBOM generation can help organizations streamline the creation and maintenance of SBOMs, ensuring accuracy and consistency across software assets.
- Integrate SBOM into Security Practices: SBOMs should be integrated into existing security practices, such as vulnerability management, incident response, and risk assessment, to enhance the effectiveness of cybersecurity measures.
- Collaborate with Software Suppliers: Organizations should collaborate with software suppliers and vendors to obtain accurate and up-to-date SBOMs for third-party software components, fostering transparency and accountability throughout the software supply chain.
Hunted Labs' SBOM Recommendations
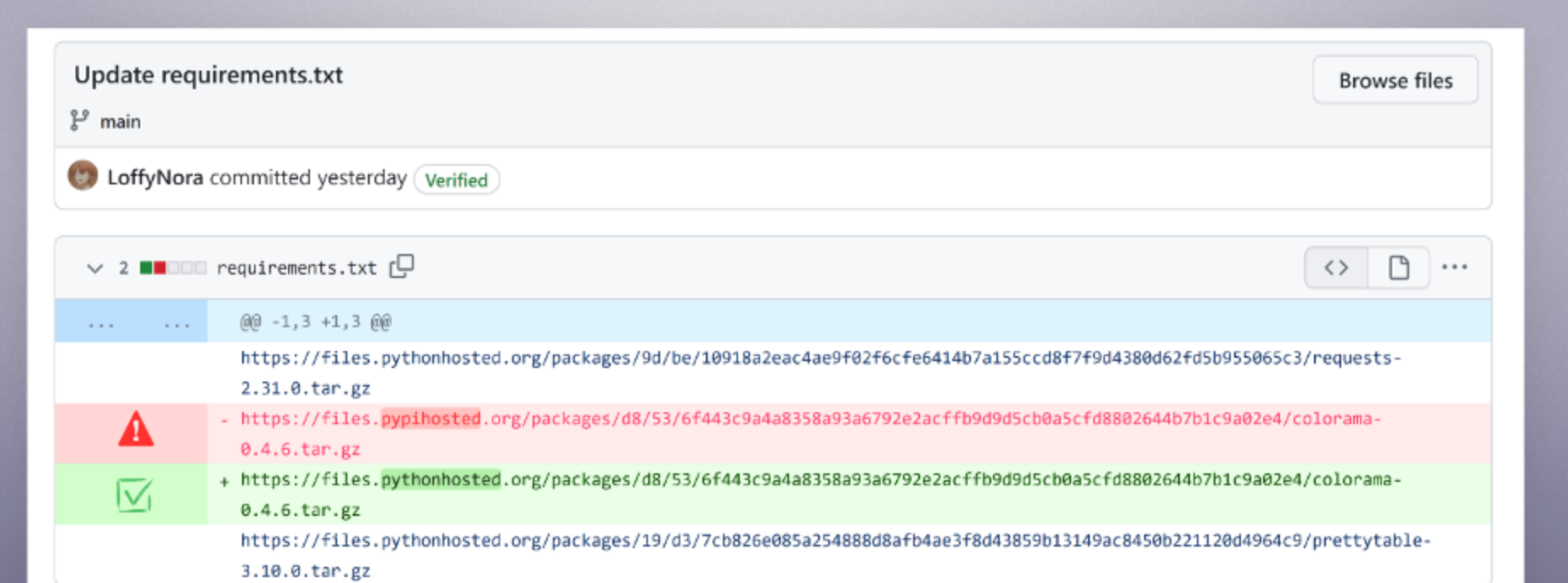
- Validate Remediation Reaches the Developers Hands: Automate the remediation at best, but worst case, validate the remediation information is accurate and makes its way back to the developer. Often, remediation information available through a series of links are available for the responsible developer to power-click on - that is remediation information, not remediation steps. The difference is multiple hours of wasted time and a diluted ROI on an SBOM.
- Hunt with SBOMs: Have the ability to hunt for a specific package in a matter of seconds. At Hunted Labs, we focus on the hunt. It’s important to just type a package identifier and identify your blast radius quickly. In actual security incidents, this can save an enterprise organization millions of dollars in potential damages. This is really useful for leveraging existing cyber threat intelligence and hunting for IoCs within your SBOM. The team that leverages third party and relevant data points to overlay on top of the SBOM has a strategic advantage in their cybersecurity posture by allowing their teams to draw additional cybersecurity insights such as continuously identifying potential IoCs or even IoAs that could be hidden within your software attack surface.
- Enrich your SBOM Data with Other Security Information: SBOM is a great data point, but nothing is the solution to every problem – no matter how many times you see it on LinkedIn. SBOMs aren’t the end all be all. Leverage third party and other security data points to overlay on top of the SBOM to identify additional cybersecurity insights such as identifying potential IoCs or even IoAs that could be hidden within an SBOM in your organization.
Conclusion
CISA's guidance on SBOMs provides organizations with a basic, yet valuable framework to enhance visibility, transparency, and accountability in their software supply chains. By implementing these best practices, organizations can strengthen their cybersecurity posture and take a step in mitigating software supply chain risks. By adopting Hunted Labs recommendations, your organization can actually build resiliency into your software supply chain, help manage your software attack surface, and reduce your blast radius by integrating SBOMs into existing cybersecurity operations. To learn more about how SBOMs can help you maneuver in the Cyber Kill Zone, check out our previous blog here.
Did We Miss Something?
At Hunted Labs, we want to be transparent about hearing different voices and perspectives from members of the community. If we missed something, please reach out!
HAPPY HUNTING!

MENU
STAY CONNECTED
Join our mailing list to stay up to date on all things Hunted Labs!
Contact Us
Thank you for your submission! You will be added to our mailing list and have all our company updates sent straight to your inbox!
Please try again later




