BATTLE TESTED. MISSION READY.
Using Bard to Secure the Software Supply Chain
SBOMs, CTI, and I
Staying ahead of potential exploits and vulnerabilities within source code is vital for organizations to outpace many of the threats persisting in the threat environment today. Luckily, using some creativity and Bard, AKA Gemini, we were able to fuse cyber threat intelligence, SBOMs, and Google Drive to offer a transformative approach to integrating cyber threat intelligence into the software development lifecycle. Today we will make Bard our cybersecurity assistant, leveraging its capabilities so that we can demonstrate how developers and security teams can proactively identify, understand, and mitigate potential vulnerabilities in your code.
There are several types of threat intelligence including:
- Strategic Intelligence: Provides high-level insights into the broader threat landscape, such as emerging cyber threats, geopolitical factors influencing cyber activity, and industry-specific risks.
- Tactical Intelligence: Focuses on specific threats and adversaries, including IoCs, malware analysis, and threat actor profiles. This type of intelligence helps organizations identify and respond to immediate threats effectively.
- Operational Intelligence: Offers real-time information about ongoing cyber threats, such as indicators of active attacks, compromised systems, and vulnerabilities in the organization's environment.

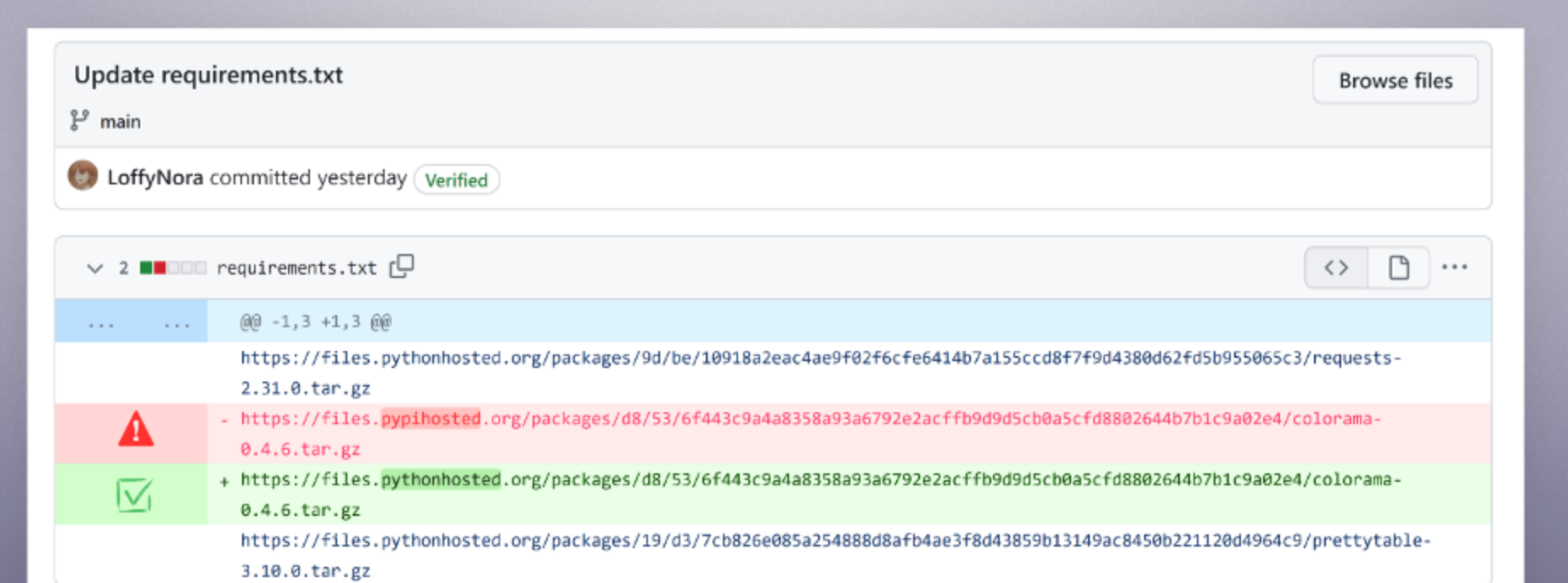
This experiment was simple. Take OSINT threat intelligence blogs and shove them in Google Drive. Take SBOMs and vulnerability scans to shove in Google Drive dumping those into txt files within Google Drive. This was pretty easy, for demo purposes, I only did 10-12 SBOMs that I knew had vulnerable packages.
Leave the rest to Bard.
Bard's ability to process vast amounts of cyber threat intelligence and contextualize it in relation to an organization's specific software environment is a game-changer. This is a great use of GenAI as it helps summarize and describe hundreds of pieces of threat intelligence contextualized as various blogs. Also, I hate reading. Bard doesn’t.
I thought of generating vulnerability scans, but that honestly would be a waste of time. Bard can tell me what is vulnerable. With access to a comprehensive database of known vulnerabilities, exploits, and threat actor tactics, Bard can analyze bits of SBOMs that I provide to detect packages that may be vulnerable to exploitation. If I baked this into a pipeline, it could easily enable teams to address issues before they can be exploited by malicious actors. Additionally, Bard can suggest relevant patches or remediation strategies, drawing from its extensive knowledge base to provide tailored remediations/recommendations. This was one of my favorite use cases. For example, even if you have 2 vulnerabilities you have to remediate, you are probably going to spend at least an hour familiarizing yourself with what the bug/vuln is, what the mitigation/patch is, why this is an issue in the first place, and what the proper next steps are. This saved me a lot of time that I would be using to power-click through scan results I received as an output from a scanner.
Moreover, Bard's utility extends beyond mere vulnerability detection. It can serve as a continuous learning tool for development and security teams, keeping them informed about the latest attack trends, IoCs, and other emerging threats. I really enjoyed asking Bard questions about different vulnerabilities tied to specific threats. In which case, Bard would return a wealth of knowledge on the APT group itself, if the group has been seen exploiting that vulnerability/package in the wild, as well as any TTP's associated with that group. This was very impressive from a context perspective, but it also helped go through hundreds of vulnerabilities flagged as “high” or “critical”, but ended up not being actively exploited and had no exploit available. This was easily assembled into a POAM that I could store for a rainy day.
Bard represents a significant advancement in the intersection of AI, software development, and cybersecurity. Its ability to analyze parts of SBOMs in the context of the latest cyber threat intelligence offers a proactive approach to identifying and mitigating vulnerabilities. As the software attack surface evolves constantly at every stage of the SDLC, tools like Bard, and Generative AI in general, will become indispensable in the ongoing effort to build truly resilient software supply chains to assist developers in understanding the applicable threats relevant to their code.

MENU
STAY CONNECTED
Join our mailing list to stay up to date on all things Hunted Labs!
Contact Us
Thank you for your submission! You will be added to our mailing list and have all our company updates sent straight to your inbox!
Please try again later



