The Russian Open Source Project That We Can’t Live Without

Hunted Labs Discovers Suspicious Origins of Ubiquitous Open Source Package
Happy Birthday, JiaTan and XZ: Why Your Software Supply Chain is Crazier Than You Think

It’s been one year since the discovery of the March 28th, 2024, XZ-utils breach and the attack that changed the open source ecosystem forever. Every day, developers around the world power a trillion-dollar global economy by contributing millions of pieces of open source code used by every organization to build and maintain their products. However, […]
How North Korea is Exploiting GitHub to Infiltrate Software Supply Chains
North Korea’s latest tactics reflect a broader trend of nation-state actors targeting enterprise and open source software supply chains.
How the Elf on the Shelf Messed Up My Software Supply Chain

With two young kids, the annual tradition of Elf on the Shelf is alive and well in my house. But, of course, the suspense and thrill of this beloved custom is taken to another level in the Smith household. It begins with the sudden appearance of a suspicious elf – usually the day after Thanksgiving […]
Software Supply Chains and the Rude Awakening that Ushered in a New Era of Intelligent Security

In the ever-evolving landscape of cybersecurity, software supply chain security has fast become a critical concern for public and private organizations worldwide. And with good reason, as crippling high-profile attacks of recent years have shown just how vulnerable entities are and the level of damage they can cause. In this blog post, we explore the […]
Why I Joined Hunted Labs: Paul Novarese, Principal Solutions Architect

My whole career has revolved around helping enterprises use open source software, and the vast majority of that time I’ve focused on security. The last few years in particular, I have been primarily focused on application security. In that time, I’ve noticed that while there has been an explosion of tools in this segment, there are […]
Where the Wild Things Are: A Complete Analysis of Jia Tan’s GitHub History and the XZ Utils Software Supply Chain Breach
Breaking down the recent XZ Utils security breach and how things came about.
Software Supply Chain Defense: Colorama, GitHub, and More
Lessons learned from the attack that targeted 170k+ GitHub users and some easy things your teams can do to protect their organization from the next one.
Understanding SBOMs and Your Software Attack Surface

Understanding why SBOMs are important, and how organizations can leverage CISA’s guidance to bolster their cybersecurity posture.
Using Bard to Secure the Software Supply Chain
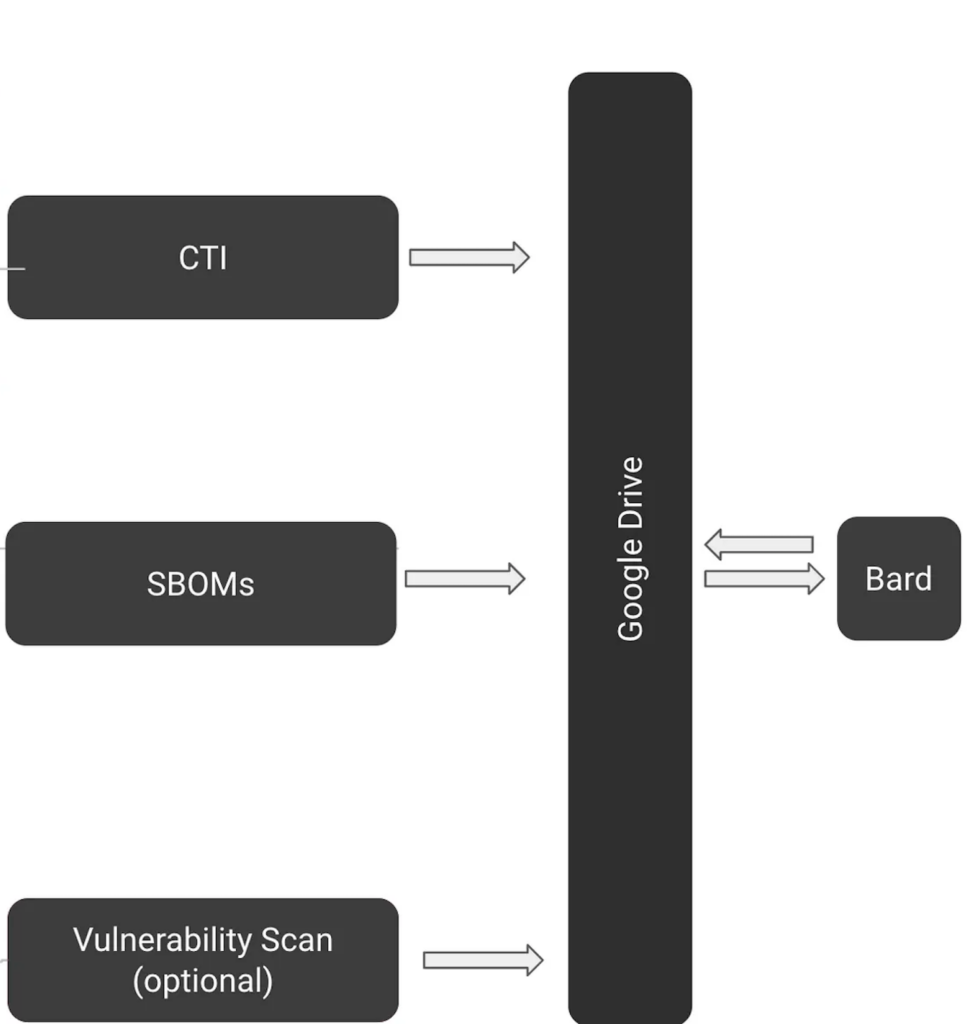
Making Bard our cybersecurity assistant, leveraging its capabilities so that we can demonstrate how developers and security teams can proactively identify, understand, and mitigate potential vulnerabilities in your code

