Safe Vibes Only: How DepsDiver Assist Secures AI-Generated Code from Foreign-Controlled Dependencies

AI coding copilots are injecting hidden dependencies from adversarial nations into your codebase without you noticing.
Introducing DepsDiver: Eliminating the Security Blind Spots in Your Dependencies

Hunted Labs is introducing DepsDiver, a new class of dependency security focused on uncovering foreign influence and code repository risk early and providing package alternatives. Dependency Risk Has Changed Open source is the foundation of modern software, but dependency decisions no longer happen the way security teams assume they do. In practice, most dependencies […]
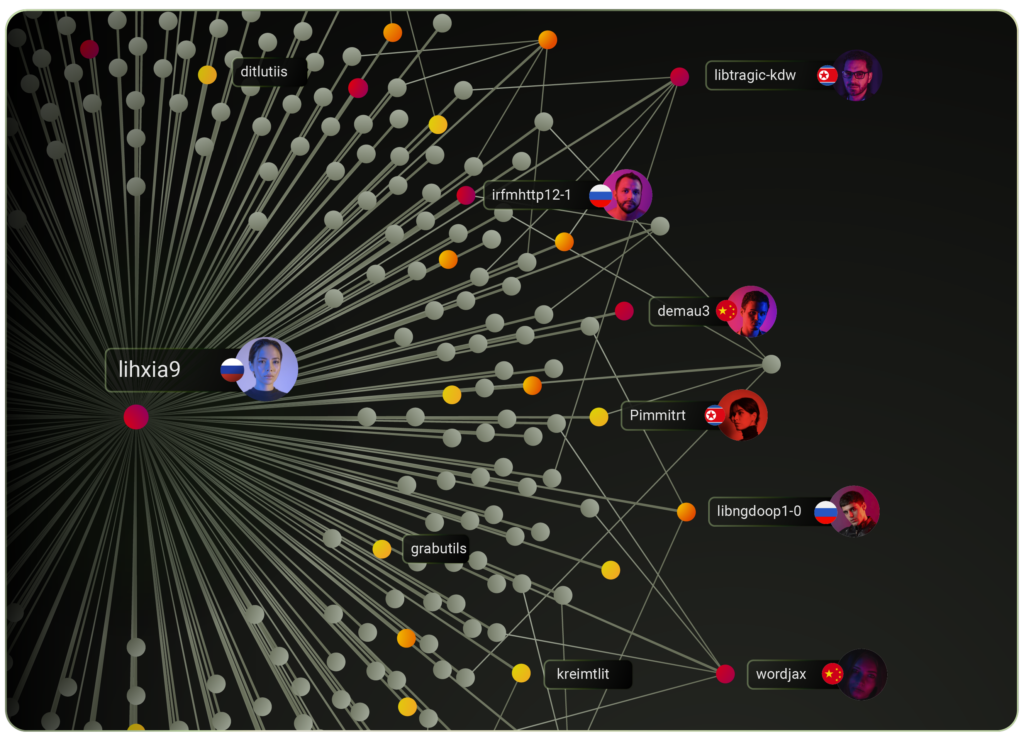
Contributor Intelligence: Why People Behind the Code Matter More Than Ever

Vulnerabilities don’t show who controls your code. Contributor intelligence exposes hidden risks in open source supply chains.
Hunted Labs’ Principles for Open Source Security

The seven principles that anchor everything we do
Popping Fast-Glob’s Hood

Solo maintainer poses supply chain risk to more than 5,000 software packages, including container images in Node.js and Department of Defense systems
Why the DoD Is Rewriting the Rules on Software Trust

If your software and hardware is being used by the DoD, your organization will need to identify and remove any foreign influence sooner rather than later.
How We Removed easyjson and Why You Should Too

As concerns grow around geopolitical risks in open source, many teams are re-evaluating dependencies like easyjson. At Hunted Labs, we took action—mapping our exposure, investigating its roots, and removing it. This post outlines our process and offers a blueprint for any team confronting hidden risks in their software supply chain.
Securing Open Source Code is a National Security Imperative

The Foundation We All Stand On The next frontier of warfare isn’t just kinetic, it’s code. Our adversaries don’t need bombs to destabilize us. They need bugs. Exploits. Manipulated commits. In an era of digital-first infrastructure, bits are bullets. And we are exposed. Every government system, hospital, energy grid, airplane, and missile defense platform relies […]
Protecting the Source: A Modern Framework for Software Supply Chain Security

Seeing the Whole Picture, from Developer to Deployment
Introducing Entercept™ to Expose Threats in Your Applications
Representing the next generation of cybersecurity attribution and open source contributor intelligence, the AppSec Platform makes the invisible visible.

